Protecting your data with smart cyber security solutions
- May 10, 2019
- Posted by: Mouad SBAYLI
- Category: Resources

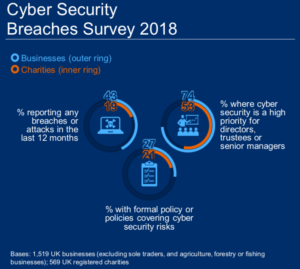
The latest research from the ONS Cyber Security Beaches Survey 2018 suggests that 42% of micro and small businesses identified at least one breach or attack in the last 12 months. Approximately 17% of those breached took a day or more to recover, losing an average of $1500.
Among the 25% of business that didn’t have any cyber security measures in place, as much as 24% thought their business was too small or insignificant to be targeted. Cybercrime doesn’t sleep, zero-day threats can attack at any time and, without the correct security processes in place, your customers and patient’s data could be vulnerable.
It’s vital that your data is protected from potentially devastating financial and reputational damage with smart and sophisticated cyber security solutions that can block threats both at the endpoint and on the web.
Products and services: Stay Ahead of Cyber Attacks with adaptive security
Ransomware continues to affect businesses in a huge way. After WannaCry and Petya in 2017, GrandCrab and Magniber were some of the biggest culprits of 2018, increasing ransomware detection in businesses by 88%*.
We offer a range of security products to protect our customers’ devices against ransomware with some of the powerful features:
- Location-aware policies
- Two-way Firewall
- Antivirus and antimalware
- Intuitive filter settings
- Email notifications
- Device and USB control.
Defend your business against prolific threats with an industry-leading, trusted solutions that gives peace of mind.
*Malwarebyte, Cybercrime Tactics and Techniques: Q3 2018.
Keep users safe when browsing the web:
First line defence against accidental visits to malicious or compromised websites starts with our product leading provider Symantec. By scanning 1.07 billion URLs per day, Symantec blocked an average of 611,141 web attacks daily due to a 2.8 growth in malicious URLs in 2017.
Using Skeptic technology to protect against new malware and web threats, Symantec Web Protect is one of the best cyber security solutions to defend your customers when browsing online.
We can provide you with licensing and management of all your users to protect them against any possible threat:
- Multi-layered antivirus and antispyware
- Secure compliance policies
- Intuitive URL filtering
- Intelligent Skeptic technology
- Roaming user support
- Detailed reporting
A multi-layered security approach is the best way to combat an increasing threat landscape. Cyber Security solutions can only predict patterns as far as their global intelligence reaches, so it’s best practise to combine those solutions with a business Continuity and Disaster Recovery (BCDR) implementation.
For your business, the financial costs and remediation following a breach can cause significant damage to their brand, leading to detrimental consequences. But with a solid BCDR solution, data breaches that occur can be rectified with little downtime.
Many small/medium businesses still rely on backing up their data on tapes and storing them offsite. For years, this proved as an effective, cheap and reliable route for SMBs, But times have changed, the cloud has evolved and restoring tapes to an offsite server is now significantly slower and can involve larger periods of downtime for your business, compared to cloud-to-cloud backup.
Before Choosing a DR solution for your business, ensure it meets the following criteria:
1. Automatic backup of critical systems and data
2. Quick disaster recovery from an easy to use solution
3. Frequent point-in-time backups
4. A failover datacentre should the primary location fall
We are Microsoft Cloud Service Provider and Acronis partner offering a solid solution to your data backups and recovery.
The benefit of working with us to manage and backup your data :
- Monitor your backups and ensure, no backup is missed out
- 3 ways to back up: Full, differential and incremental backup options enable you to back up customer data efficiently, with the latter only storing blocks of data that have changed since the last backup.
- 4 retention options: Choice of retaining recovery data either daily, weekly, monthly or yearly.
- Ultra Secure: Backup your data to our cloud storage provided by Microsoft and Acronis, leaders in security and safeguarding customer data. Your data is encrypted before stored on the cloud. Unlock data with your encryption key that only you knows.
Uninterrupted access for users with a site recovery service.
Our solution will help you implement a simple BCDR solution for your customers, not only with this help ensure business continuity by keeping workloads running during an outage, it also replicates workloads running on physical machines and Virtual Machines (VMs) from a primary site and transfers them to a secondary (or failover) location. Once the primary site is up and running again, you can transfer the data back to it.
The benefit of using our site recovery solution:
Spend less time on maintenance: No need for a secondary datacentre, you can replicate on-premises VMs and physical servers to the Cloud without hassle.
Safely test disaster recovery on applications and workloads between.
Easy to customise: Recovery plans can be customised and easily sequence the failover of applications or workloads.
Secure Cutomer Data and meet compliance regulations :
As a Microsoft partner we offer products and services that will ensure the security and protection of customer data first. Microsoft holds 47+ security and compliance certifications more than any other cloud provider. The company is committed to securing customer data with robust solutions and ensuring data privacy is always held in the highest regard.
When it comes to governance and compliance, our duty is to ensure where your data is stored and who has access to it and when. Some businesses believe that if they host their data with Microsoft Azure, it’s no longer theirs and is mixed with other companies on the same network. This is simply not true. Microsoft ensure that your data remains your own, in a private space that you rent each month on a multi-tenant environment. Think of it as an apartment complex with a landlord, they are liable to protect and secure the area as best as they can.
How Microsoft handles customer data :
1. Geographic storage locations : For data litigation purposes most Azure deployments for your data will want to be stored in Morocco or closed location such as France. Microsoft will not transfer data outside the geo specified, though they will transfer data between regions, particularly if an outage should occur.
2. Access to customer data : Access to any customer data via Microsoft personnel is restricted and is only accessed when necessary to support queries around Azure; e.g. troubleshooting etc. Any access is controlled, logged and revoked when it’s no longer required. Microsoft follows stringent processes which are verified by accredited auditors.
3. Customer data is protected in the EU : Microsoft is Safe Harbour certified under the U.S Department of Commerce, allowing for the legal transfer of EU personal data outside of the EU Geo, which is submitted to Microsoft for processing, this means that data can be transferred outside of the designated Geo but will only be processed in line with the EU Data Protection Act and GDPR.
4. Law enforcement requests :Microsoft will not disclose customer data to a third party – including law enforcement or government entities -except when directed by the customer or if required by law to do so from a court order or warrant. If data is requested, Microsoft will direct the third party request back to the customer with basic contact information.
Email Security – Cybercriminals are getting smarter:
A Recent rise in social engineering attacks fooled even the most skilled tech users, with many failing to realise that their CEO doesn’t need Google Play vouchers, or that urgent bank transfer to secure a deal isn’t real.

These emails -known as business email compromise (BEC) attacks – use legitimate credentials that have either been leaked in previous breaches or are available in the public domain. Targeting specific individuals, users can be lulled into a false sense of security and will happily validate information to cybercriminals when they believe they are someone else that they know and trust.
In 2019, Giacom predicts that social engineering emails will get more personal, weaponised and sophisticated. Ensuring you have a powerful email security solution integrated with Office 365 will not only help block attacks before they reach their mailbox, it can also warn of potential malicious links or attachments.
At For Better Health, we partner with Giacom to offer a range of email security products that will protect your Office 365 emails and warns you of any malicious attacks. Our offerings include management and licensing of VadeSecure a leader in the protection of Office 365 mailboxes and DeliverySlip for seamless email ecryption.
Advanced Email Security for Office 365 by Vade Secure blocks major zero-day malware and ransomware, spear-phishing and business email compromise (BEC) attacks by identifying and analysing every email to predict malicious patterns. With 24/7 global threat intelligence, it’s protection that lives inside Office 365, so you don’t have to:
- 360 Email protection
- Identity Match
- 99.99% spam capture rate
- Time-Bombed URL Protection
- Safe unsubscribe
Protecting Sensitive business or financial information over email with secure encryption from DeliverySlip. Used by more than 10,000 organisations and 5 million+ users worldwide, DeliverySlip makes it easy for your employees to hit send without worry by providing one click email encryption directly inside their office 365 or Outlook. Plus they can easily transfer large files and access them through a mobile browser or the Androird, iOS and Windows apps. Our client can feel safe in the knowledge that they’re using bank-grade encryoption to view their emails securely while reducing their risk of phishing, malware and spam.
- Encrypt and go
- Large File transfer
- E-discovery and E-audit
- Real-time tracking
- Sign document on the go
- Signle sign-on support
- www.forbetterhealth.co.uk
- services@forbetterhealth.co.uk
- https://twitter.com/fbhmorocco
- https://www.instagram.com/fbh.morocco/
- https://www.facebook.com/ForBetterHealthMorocco
- Mobile : 07 00 71 99 91
- Fixe : 05 21 21 00 32

